Privilege Escalation & RCE
تفاصيل العمل
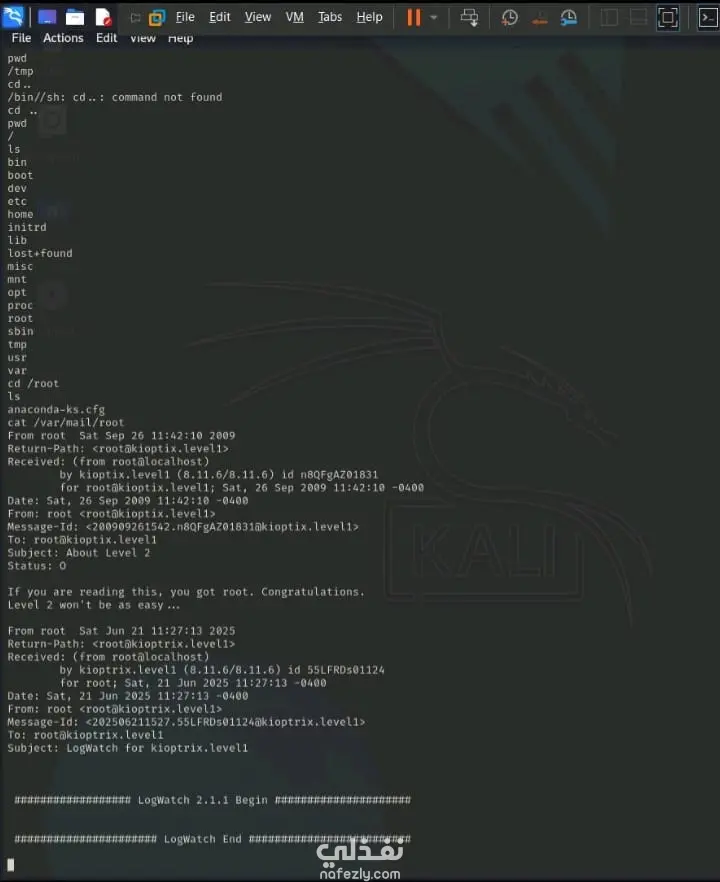
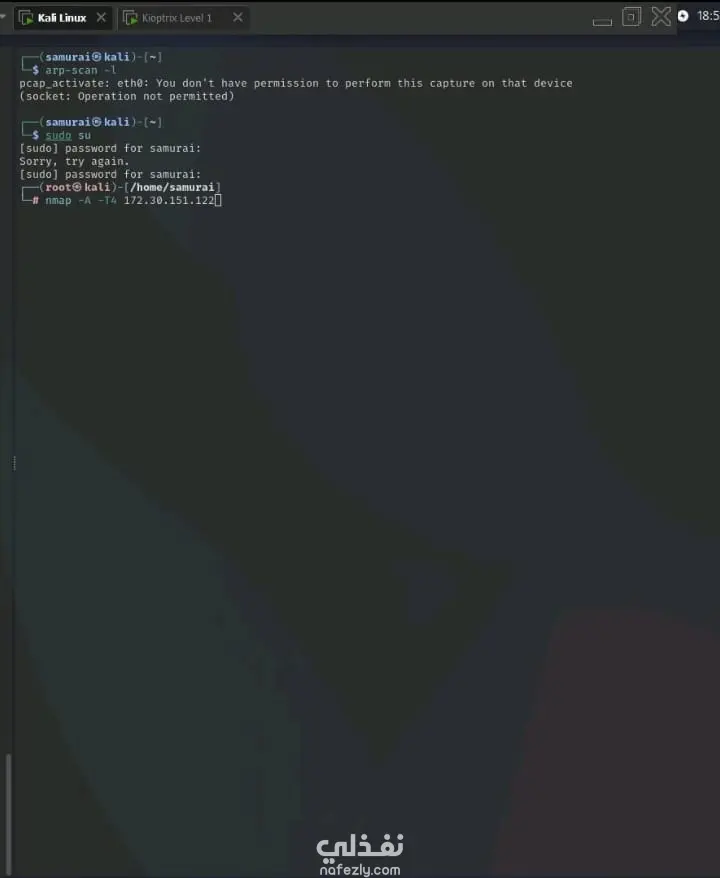
Role: Penetration Tester (Practical CTF challenge) Summary: Performed full exploitation of a vulnerable virtual machine to achieve remote code execution and privilege escalation to root; documented findings and remediation steps. Highlights / CV bullets Performed comprehensive reconnaissance and full-port scanning to discover exposed services and identify attack surface. Enumerated services and researched version-specific exploits, locating a critical Samba vulnerability (call_trans2open, CVE-2003-0201). Configured and executed an exploit using Metasploit (exploit/linux/samba/trans2open), delivered a payload, and obtained a root shell on the target server. Produced an exploitation timeline and remediation recommendations, emphasizing patching, service hardening, and monitoring for legacy services. Verified post-exploitation impact and documented lessons learned to improve future assessments. Tools & Techniques Nmap (full port scan / service discovery) Searchsploit / CVE research (vulnerability identification) Metasploit (exploit module, payload delivery) Enumeration & manual analysis (service/version fingerprinting) Outcome / Impact Demonstrated real-world RCE and privilege escalation against legacy services, reinforcing the critical risk of unpatched/obsolete software. Delivered actionable remediation guidance: upgrade Samba, apply vendor patches, restrict exposed services, and implement continuous vulnerability scanning.
بطاقة العمل
طلب عمل مماثل